Achieve ISO 27001
What is an Information Security Management System (ISMS) and how does it relate to ISO 27001?
I became involved with information management standards almost 20 years ago. Initially was very confused with all the jargon and abbreviations auditors and consultants were throwing at me. Management system standard, IMS, ISMS, ISO 27001, 27002, 27005, 27k, accreditation, certification, UKAS, IAF… eventually they all made sense – but one that took slightly longer to fall into place is ISMS.
ISMS confused me because it seems to mean different things to different people. To some people it means a software application, to some it is synonymous with ISO 27001 and to others it is synonymous with some other information security standard!
This article is for you if you:
- are new to information security and the world of information management standards.
- want to unpick the jargon.
- need a clear view of what ISMS means and how it relates to ISO 27001.
- want information to help decide whether you should implement an ISMS with ISO 27001.
I will cover the following topics:
- What is an ISMS?
- Why should you have an ISMS?
- What is ISO 27001 and how does it relate to ISMS?
- Can ISO 27001 be implemented in a startup, small business or charity?
- Can we implement ISO 27001 on our own, without consultants?
- How to implement an ISMS using ISO 27001
- What are the ISO 27001 requirements?
- What is an information security policy?
- How much does ISO 27001 cost?
- Will I need to invest in new technology?
- How long will it take to implement?
- What’s the difference between compliance and certification?
- How do I get ISO 27001 certification and why?
Reading time: 13 minutes
What is an ISMS?
Firstly, before diving into describing what an ISMS is, I’d like to clarify what a Management System is. The International Standards Organisation defines a management system as follows:
“A management system is the way in which an organisation manages the interrelated parts of its business in order to achieve its objectives.”
In practice this means a management system is a set of agreed processes, policies and procedures used by an organisation to ensure it can improve and perform the tasks necessary to achieve its objectives. The objectives could be in relation to its environmental performance, quality of products and services, occupational health and safety risks or information security risks.
Consequently, an information security management system refers to a set of agreed processes, policies and procedures which manage the risks to the security of its information and helps it achieve its objective of protecting that information.
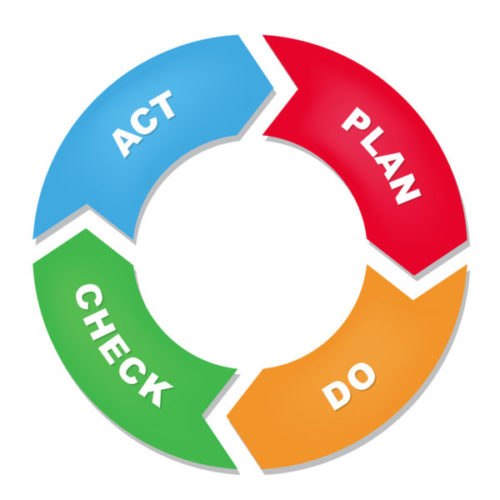
Management system standards, in addition to providing a blueprint for management systems, assume that in order for the organisation to achieve its objectives, it needs to improve. They are therefore based on Deming’s Plan-Do-Check-Act model of continuous improvement:
Plan: Assess your risks, define roles and responsibilities and agree processes, policies and procedures that will help you achieve your objectives
Do: Implement those processes, policies and procedures
Check: Define measures, monitor them and perform internal audits to see if the processes, policies and procedures are followed and are working as expected
Act: Based on the monitoring and internal audit results obtained in the previous step, make decisions to either maintain the processes, policies and procedures or amend them
Why should you have an ISMS?
- Give confidence to your clients that their information is secure – With an ISMS in place you will have answers to all their questions and will be able to provide evidence that you take information security seriously and manage the risks to it pro-actively.
- Reduce the cost of managing information security – Rather than implement the latest defensive technology that might not be necessary for you, an ISMS will give you a consistent risk-based approach to underpin all your decisions.
- Align all your employees in the same direction – As with any management system, an ISMS provides a clear framework that everyone in the organisation can follow. It will increase employee awareness of security risks across the board, not just in IT. Information security becomes part of everyone’s day-to-day way of working.
- Increase accountability and your governance maturity – An ISMS enables you to put a clear governance structure in place, clarifying the roles and responsibilities at all levels as well the reporting lines.
- Enable continuous improvement – Management systems are based on a continuous improvement model which uses regular internal audits to highlight items of non-compliance and areas for improvement.
What is the ISO 27001 standard and how does it relate to an ISMS?
The very first sentence in BS EN ISO/IEC 27001:2017 (that’s the full official reference to ISO 27001 in the UK) is: “This International Standard has been prepared to provide the requirements for establishing, implementing, maintaining and continually improving an information security management system.”
In other words, ISO 27001 is a “How-to” guide to having an ISMS.
While there are quite a few types of ISMS, I have chosen to be an ISO 27001 consultant and I favour this international standard over others. Why? Because it’s recognised internationally, applies to all types of information (digital and paper-based) and can be scaled in accordance with the needs of the organisation implementing it, regardless of its type or size. The British Standards Institute have certified “one-man–bands” all the way up to global organisations with tens of thousands of employees.
If you still have questions or are unsure of ISO 27001 and its benefits read our ‘What is ISO 27001 certification and how much does it cost’ article.
Can ISO 27001 be implemented in a startup, small business or charity?
Yes. The standard doesn’t prescribe which procedure or technology you need to have. It doesn’t expect a small organisation to invest large sums it cannot afford in complex technology. Instead it expects that an information security management system implementation is scaled in accordance with the needs of the organisation.
Our article ‘Who needs ISO 27001 certification’ goes deeper into this question.
Can we implement ISO 27001 on our own, without consultants?
In my experience, the world of international and British standards is baffling to the uninitiated. It took me a number of years to understand everything auditors were telling me. Auditors seem to speak a completely different language to the rest of us and often assume you understand. Combine that to the world of information security which is moving at the speed of light and encompasses a vast amount of knowledge, and you have a recipe for confusion.
In light of that, yes, it is entirely possible to implement ISO 27001 without consultants if:
- you have enough technical knowledge internally to understand where the risks to information security are and how to go about minimising those risks.
- you are prepared and have time to read on the topic of ISO 27001.
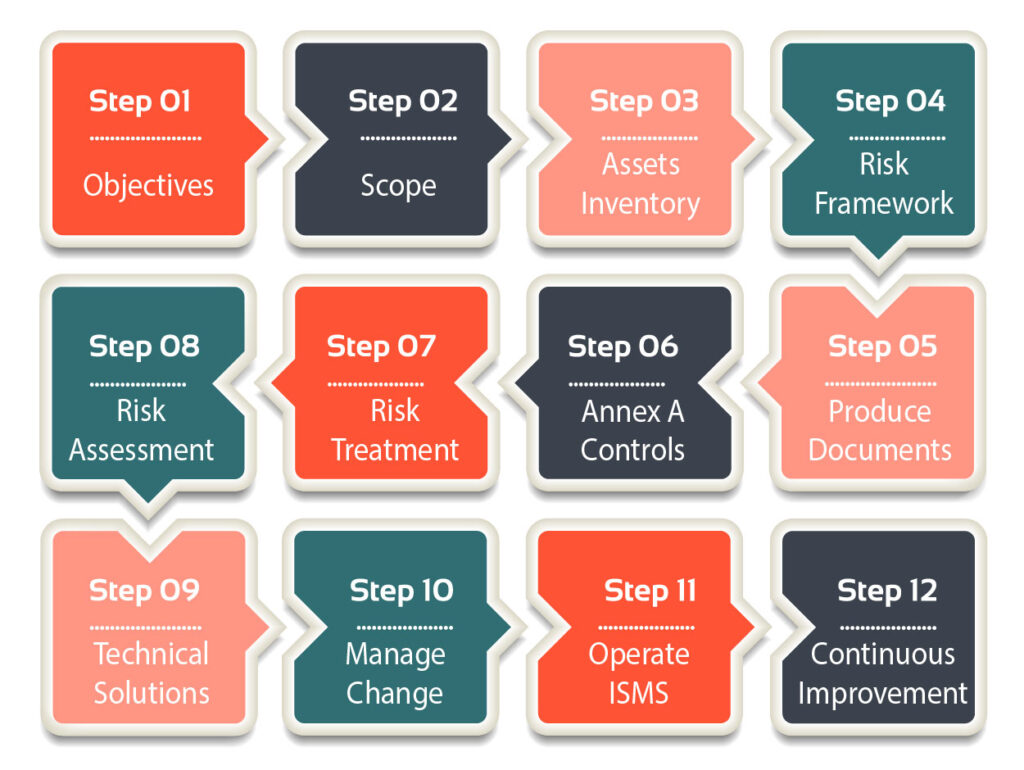
How to implement an ISMS using ISO 27001
The diagram below gives you a high-level overview of our 12-steps approach to implementing ISO 27001. If you want more details, we have a separate article on this topic, please have a look at How to implement ISO 27001.
What are the ISO 27001 requirements?
In a management system standard, requirements are indicated by the word “shall”. Anything that follows “shall” must be in place for a certificate to be given. For example, section 6.1.2 a) of ISO 27001 reads as follows:

There are four requirements from this extract:
- An information security risk assessment process must be defined
- An information security risk assessment process must be applied
- The process must establish and maintain criteria to guide decisions on which risks to accept
- The process must establish and maintain criteria to guide decisions on when to perform a risk assessment
Overall, there are over 200 such requirements. At a high level the key aspects they cover include the objectives of the ISMS, scope, roles and responsibilities, competence, communication and awareness, Information Security Policy, Risk Management Framework, documentation, performance evaluation and continuous improvement.
What is an information security policy?
The Cambridge Dictionary defines a policy as “a set of ideas or a plan of what to do in particular situations that has been agreed to officially by a group of people, a business organisation, a government, or a political party”.
In the context of ISO 27001’s ISMS, an Information Security Policy is, therefore, a plan that defines what to do to maintain the security (i.e. confidentiality, integrity & availability) of information, which has been agreed by an organisation.
It generally contains the scope, objectives, a commitment to keep information in scope secure and a commitment to continuous improvement. It has to be formally documented, be communicated within the organisation and be available to interested parties as appropriate (e.g. to customers).
How much does ISO 27001 cost?
There are four sources of costs to consider when assessing the budget required and putting a business case together.
- Cost of certification: This is based on the number of days a certification body will take to audit your ISMS. The minimum number of days is prescribed by Annex B of ISO 27006 and depends on the number of employees in scope. It starts at 1-5 employees and certification cost in that bracket is likely to be around £3,000 to £5,000 for the 3 years your certificate will be valid.
- Cost of technical solutions required: This depends on the results of your risk assessment, the chosen risk treatment controls and the current status of your information security. For this reason it is very difficult to budget for ISO 27001 before you’ve done the risk assessment.
- Cost of internal resources: While the cost of existing employees is not an additional cost, they will likely spend 20-60 person days. Depending on your cost allocation policy, you may need to factor this in.
- Cost of consultancy and/or training: Depending on the current level of knowledge on implementing management system standards and information security, you may need to hire consultants or send staff on training courses.
If you want to estimate your cost of ISO 27001, try our cost calculator!
Will I need to invest in new technology?
This very much depends on what you currently have in place and the results of your risk assessment, but the short answer is yes, you probably will need to invest in technology solutions.
To help answer this question better, below is a diagram of the 14 categories of controls in Annex A which you must consider. It is not a requirement to implement them all, but if you choose not to, it is a requirement to justify why you don’t think they are necessary.
Note that when deciding on controls to implement, the relative costs and expected benefits of each control, considered both individually and in relation to other controls, should be taken into account. That’s why ISO 27001 is scalable and can apply to very small micro-businesses as well as large global organisations.
How long will it take to implement?
The certification process for ISO 27001 requires two audits to take place, 2-3 months apart.
- The first audit (Stage 1) verifies that the documentation you have put in place conforms to the standard to make sure all requirements are covered.
- The second audit (Stage 2) verifies that the controls are in place and working, policies and procedures are adhered to and ISMS activities are being tracked and implemented.
Getting ready for the Stage 1 audit can take as little as 4-5 weeks if your organisation is small, you have people with time and a good base to start from.
However, if you consider the lead time to choose a certification body and obtain a date from them, the time it will take to do your risk assessment and implement the controls, you will do exceptionally well to certify (i.e. pass the Stage 2 audit) in less than 6 months, even if you have consultants helping you.
A more realistic timeframe is 6-12 months, or even 18-24 months if the scope is large and includes multiple locations and/or thousands of people.
What’s the difference between compliance and certification?
You may have heard the phrase “we comply with” or “we work in compliance with”. I’ve often heard these phrases used, particularly in reference to BS 10008 (Evidential weight and legal admissibility of electronically stored information – see our blog on this standard if you want more information on it).
They are often used in tender responses when the tender documents specify a certain standard is required but the respondent does not have external certification, i.e. cannot produce a certificate issued by a certification body.
Certification by an external body is not necessary to comply with a Standard. In fact, most standards published by the British Standards Institute (BSI) do not have a formal certification scheme. Only a few have. Where there isn’t an official scheme, organisations self-certify.
In summary, “we comply with” generally means an organisation has self-certified. On the other hand, “we are certified” means an accredited external body has audited us and confirmed that we do indeed operate in compliance with a standard.
Which one is best? While technically speaking there is nothing wrong with self-certification, in reality obtaining certification by an external body brings compliance to a completely different level. It is all very well going through the implementation process, writing all the policies and procedures and rolling them out, but if no external body comes to scrutinise what you are doing, then it is very much like marking your own exam! With all the best intentions in the world, the level of rigour just isn’t the same.
How do I get ISO 27001 certification and why should I get certified?
In the majority of cases, organisations embark on the 27001 journey because customers are requesting a certificate. Self-certification is therefore not really an option. In my opinion, external certification is extremely valuable. It brings compliance to a whole new level and is the engine for continuous improvement. There’s nothing quite like annual audits from an external body to align opinions, avoid complacency and speed up decision making.
You do however need to select a reputable certification body who are themselves accredited to ISO/IEC 17021-1 by the relevant authority. Otherwise your certificate might not be accepted by clients and/or in tenders. In the UK this is the United Kingdom Accreditation Service, which is itself a member of the International Accreditation Forum (IAF). The IAF has a list of similar bodies worldwide.
Key takeaways
An information security management system (ISMS) refers to a set of agreed processes, policies and procedures which manage the risks to the security of an organisation’s information and helps it achieve its objective of protecting that information.
ISO 27001 is one type of ISMS. It is a “How-to” guide to having an ISMS. It’s an international standard recognised globally and can be scaled up to global organisations with thousands of employees; or down to one-man-bands.
Implementing an ISMS using ISO 27001 will allow you to sell to clients who demand certification, such as public bodies and large businesses.
Implementing ISO 27001 is likely to take between 9 and 24 months: depending on the size of the organisation, the level of standard and information security knowledge internally and whether external consultants are involved or not.
The cost of implementing an ISMS with ISO 27001 will likely come from the following sources:
- Cost of certification
- Cost of technical solutions you’ll need to mitigate your key information security risks
- Cost of internal staff who will implement the ISMS and manage it on an on-going basis
- Cost of external consultants and/or training courses for your staff.
Start with buying the standard and reading it.

Elisabeth Belisle
Elisabeth is an Associate Consultant of the British Standards Institute (BSI), a BSI qualified ISO 27001 Lead Auditor and member of the Standard Committee responsible for the publication of the BS 10008 Standard.
Elisabeth can help you decide if ISO 27001 is for you and support you through its implementation, all the way to certification.




